Avast Business first published the Mobile Workforce Report in 2018, surveying small business employees in the UK and the US to provide insight into habits, preferences and productivity when working remotely. The report also investigated the level of trust employers had in their employees to complete their tasks and work efficiently when outside of the traditional office environment.
In the years since, remote working has moved from a future consideration to a present and key aspect of modern life. As the concept of remote working becomes normalized, we have explored the impact this change is having on small business security – such as ensuring staff awareness of cyberthreats, delivering effective best practice training, and supplying staff with secured devices.
The Mobile Workforce Report 2021 survey asked 1,000 IT decision makers and 2,000 small and medium-sized business (SMB) employees across the UK and Germany about the challenges of managing remote working and the emerging security concerns.
Key findings
-
The top three concerns for IT decision makers are:
- Unsecured connections
- Managing security software
- Unsecured devices
- 56% of IT decision makers are more concerned about security in their company since the pandemic began
- 33% of employees working from home are using personal devices that have no security controls on them to connect to their business network
- 24% of companies have allowed or encouraged employees working from home to use personal devices due to a lack of resources
- 36% of workers say their company did not supply remote working guidelines
- 28% of workers say they have been more relaxed about IT security while working from home
The security challenge of flexibility
The benefits of remote working for employees – greater flexibility of hours and improved work-life balance – are well-documented. However, the speed with which working practices have changed was entirely unexpected, meaning that security professionals are rapidly adjusting to more remote workforces and the resulting security threats this change reveals. The following sections will look more in detail at how the transition from office to home has contributed to the growth in security concerns among SMB decision makers.
Setting the scene: The normalization of remote working
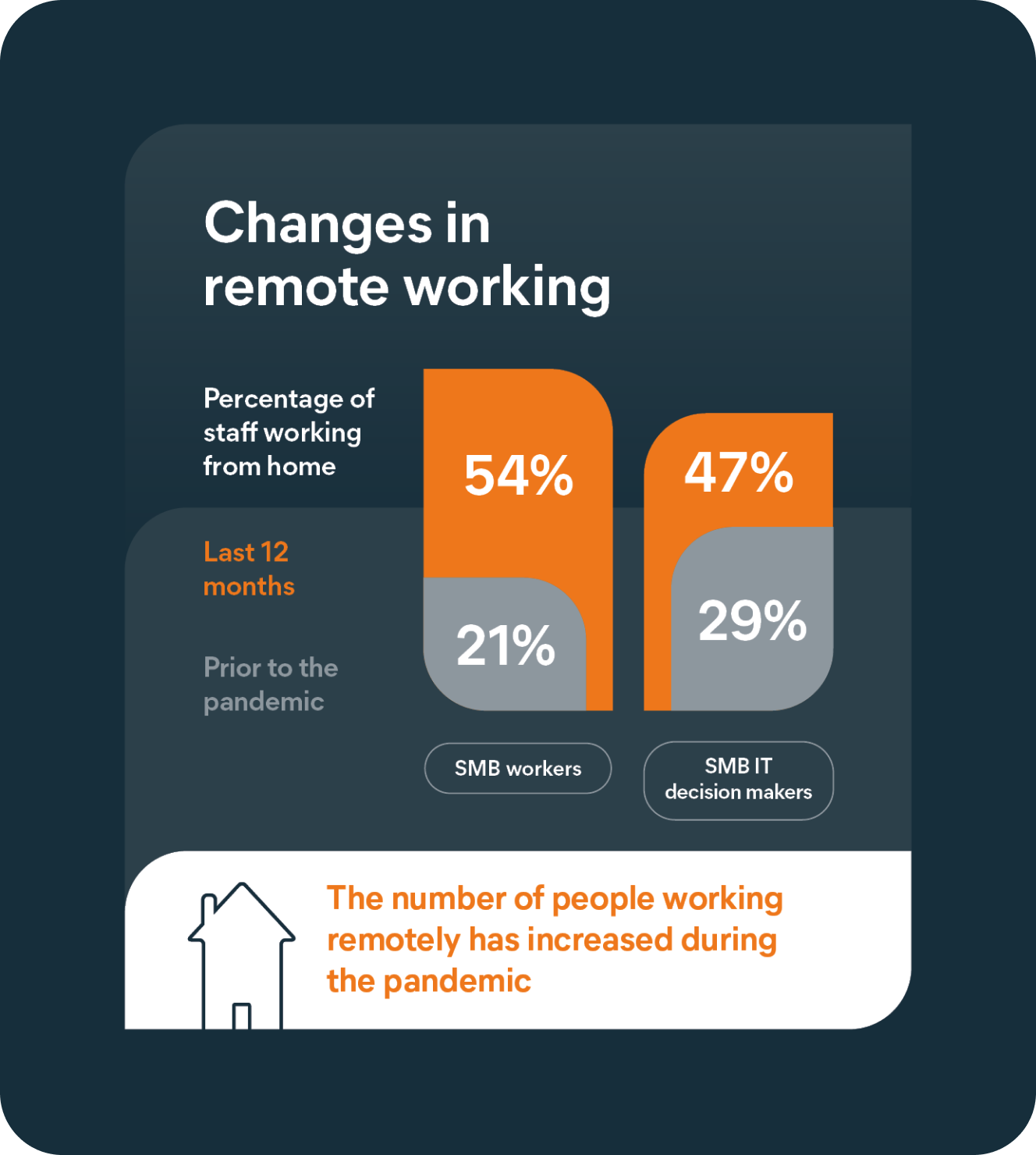
Pre-pandemic, 21% of SMB workers worked from home. This figure has more than doubled, reaching 54%. While proportionally smaller, the number of IT decision makers working from home has also seen a significant increase, rising from 29% pre-pandemic, to 47% in the past year.
Adopting these new ways of working for more than a year has forced people to adapt to completing their work remotely. As a result, COVID-19 has changed the way that companies and their employers view the workplace. Business infrastructures are no longer limited to a bank of company-supplied desktops and laptops and approved network connections.
Many will return to the office as restrictions ease, but it seems that the idea of hybrid working is established. Companies must now expect or pre-empt requests for remote working from many of their employees.
For IT executives, this ongoing normalization of working from home is causing network perimeters to widen beyond one or two offices to include Wi-Fi connections, mobile devices, and personal laptops beyond the tight control of the business.
The task of securing an ever-expanding attack surface (the range of access points a hacker could use to attack a network) must become a strategic priority for any business to protect itself and its customers from a cyberattack or data breach.
Covid-19 has completely changed the way that companies and their employees view the workplace.
Securing the network perimeter: Challenges and concerns
While many IT decision makers feel that their company did well to keep remote workers secure in an unprecedented situation (76%), more than half (56%) remain concerned about the overall level of security at their company since the pandemic began.
Businesses did and continue to do their best, but this does not mean that they were able to secure their entire network perimeter to a sufficient level. In fact, 59% of decision makers said it is difficult to keep up with securing employee devices when they are working from home – and cybersecurity is only as strong as the weakest link.
Understandably then, the level of concern is highest among businesses with a larger number of staff. 73% of those surveyed from SMBs with 100-300 employees said their concern is growing, compared to 34% of SMBs with 2-5 employees.
While a small company may have less budget and fewer resources, they also have fewer devices to manage. In contrast, if employees of larger-scale SMBs are using personal devices to access the network remotely, the business could struggle to ensure that each device and connection is authorized and correctly configured.
Educating staff on how to avoid unnecessary risks and use their devices safely can help to bridge this gap, although there are also growing concerns about how this can be effectively implemented long-term. More than half (55%) of the decision makers we surveyed believe it is difficult to keep employees educated about cyberthreats and how to avoid them. Applying best practices and achieving even a minimum level of security training for existing and new employees poses a significant ongoing challenge.
The rising threat of Shadow IT
Shadow IT is the connection of devices to the company network or use of unauthorized software (including cloud-based applications and SaaS) without the knowledge or permission of the IT department. It is an issue that will be familiar to IT staff within large businesses and enterprises, but due to the increased reliance on remote connections and cloud-based services, it’s now an area of increasing concern for small businesses.
The biggest challenge with Shadow IT is not just that the software and devices are unauthorized, but that they are not known to the IT department.
In many cases, the employee responsible for the connection will not understand the security risks of their behavior. The actions could be as simple as logging into a company social media account with a personal device or using a file-transfer tool that they are familiar with instead of the company’s preferred tool.
No matter how innocent the use of Shadow IT may be, it widens the company’s attack surface and means that connections are not being monitored on a network that otherwise appears to be secure.
This gap in security poses an ideal opportunity for malicious hackers to gain entry to the business network and increases the risk of an accidental data breach.
The biggest challenge with Shadow IT is not just that the software and devices are unauthorized, but that they are not known to the IT department.
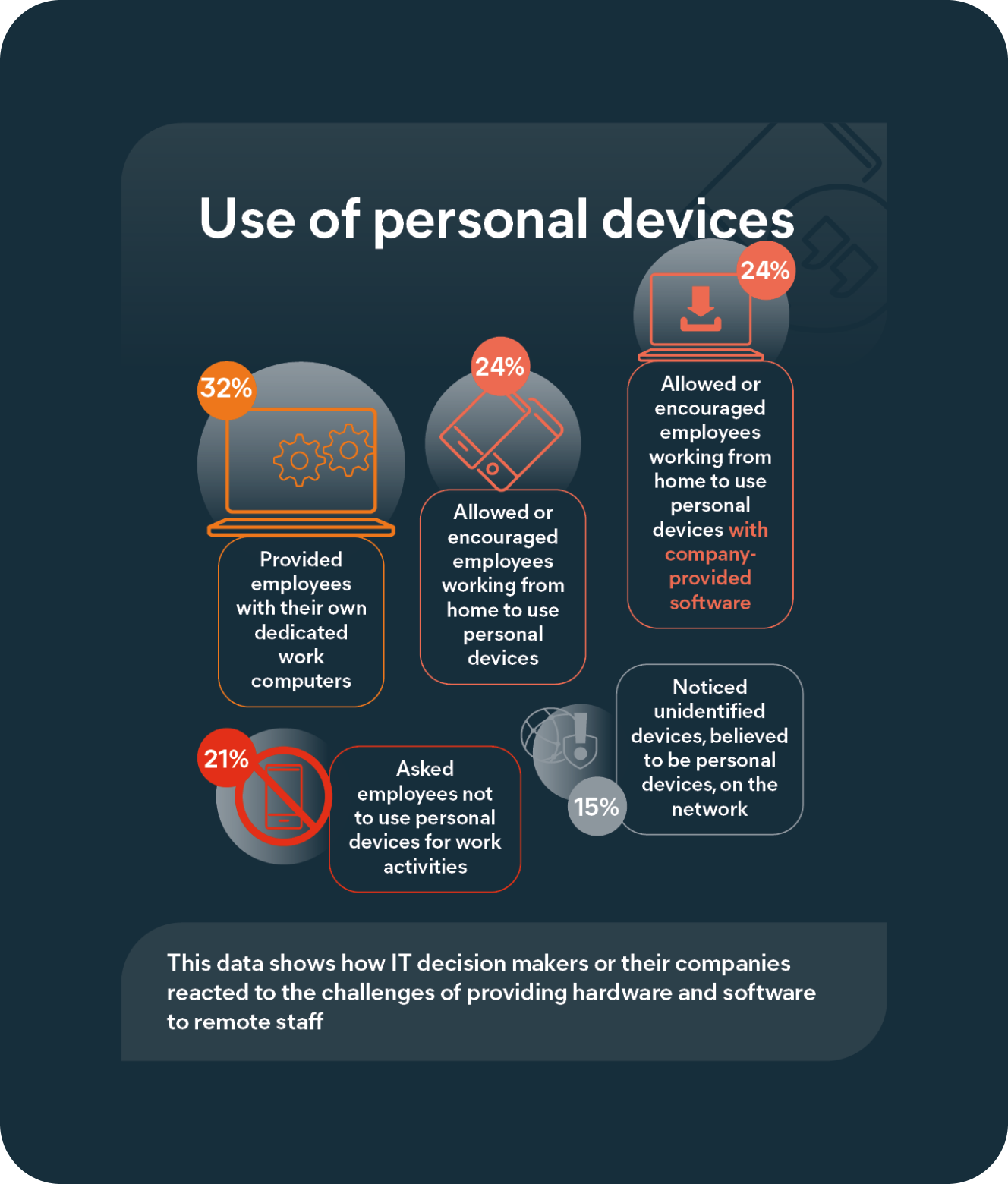
Only one third (32%) of IT leaders said that their employees were provided with their own dedicated computer for working from home, meaning the majority of those surveyed did not supply staff with secure devices – increasing the risk of Shadow IT and causing security blind spots.
Sometimes this was due to resource limitations – 24% said their company had either allowed or encouraged employees to use personal devices for remote working because of the difficulty of supplying hardware. However, lack of training also plays a role, with staff unaware of the importance of installing security software and notifying IT of their network usage.
Worse still, 33% of IT decision makers admitted to knowing their employees are connecting to the company’s IT network using personal devices that have no security controls.
While workers may have invested in products to make remote working as comfortable and productive as possible, connecting new technology and devices to the business network can create a host of avoidable security challenges.
In most cases, Shadow IT is unlikely to be malicious and is more often related to a lack of resources and training. If employers underestimate the threat, staff are unlikely to prioritize security. For a prepared workforce, Shadow IT is an avoidable threat.
Cybersecurity basics: The importance of a vigilant workforce
A 2020 study by Stanford University Professor Jeff Hancock revealed that 88% of data breaches are the result of human error. This could be through downloading an unverified application, not applying security patches, or connecting to an unsecured network. In each of these cases, improved levels of training can ensure that all staff are working with the same minimum level of understanding around security best practices. With the right teaching, employees can be one of the most valuable tools for protecting your business’ network and data.
However, an alarming 28% of workers say they have been more lax about IT security while working from home during the pandemic. It is understandable that employees may have become comfortable in their new working environments, but any complacency underlines the importance of setting up regular training sessions around security best practices.
Results from our survey show that IT decision makers are struggling to engage with remote workers on issues of security. 55% agreed that it is difficult to keep employees educated about cyber risks and how to avoid them while they are working from home. While efforts may have been made, 36% of workers reported that their company did not provide them with remote working guidelines during the pandemic.
In these cases, employers must do more to promote cybersecurity awareness by setting out security requirements and expectations for all remote staff. From there, resources can be provided to further engage the workforce and encourage employee buy-in.
Your employees are one of the most valuable tools in protecting your business’ network and data.
Employers can share tools like the Cybersecurity Quiz and Learning Resource by Avast Business to help their employees understand cybersecurity fundamentals and identify knowledge gaps.
Cybersecurity is essential to SMBs and with ENISA (the European Union Agency for Cybersecurity) estimating that there will be four times more supply chain attacks in 2021 than in 2020, the human aspect of security is becoming more critical to protecting data. Employees who lack cybersecurity awareness are putting their business and its customers at risk. However, it is the employer’s responsibility to emphasize the importance of cybersecurity basics and ensure that security is front of mind for their employees. Failure to provide training and security policies implies that security is not important, continuing the dangerous trend of a workforce feeling more relaxed about network security.
Summary
While the pros and cons of a more mobile workforce will continue to be debated, it cannot be denied that remote working is now a permanent consideration for businesses of all sizes.
There are concerns from IT professionals about the scale of the rapidly growing attack surface and the unknown factor of Shadow IT, but managing these challenges is a task for all staff.
- Employees need clear and up-to-date training to understand the security risks that occur during a typical working day. An actively aware workforce will be empowered to flag suspicious activity, or even mistakes, as early as possible, allowing IT staff to step in and manage the threat.
- Revised working from home policies can emphasize how important security is to the business and raise awareness of unsafe activity – with the aim of minimizing human errors and reducing the threat of Shadow IT.
- An effective cybersecurity policy can include the implementation of controls and cybersecurity software on all devices – especially those which connect to the business network remotely.
With an educated workforce, clear guidance and policies, and an effective business antivirus solution, the security risks of a mobile workforce can be managed, and remote working can be recognized for the benefits it brings to productivity and employee well-being.